Adding fine-grained access control
In this activity, we will add fine-grained access control to allow users access to S3 resources based on their department.
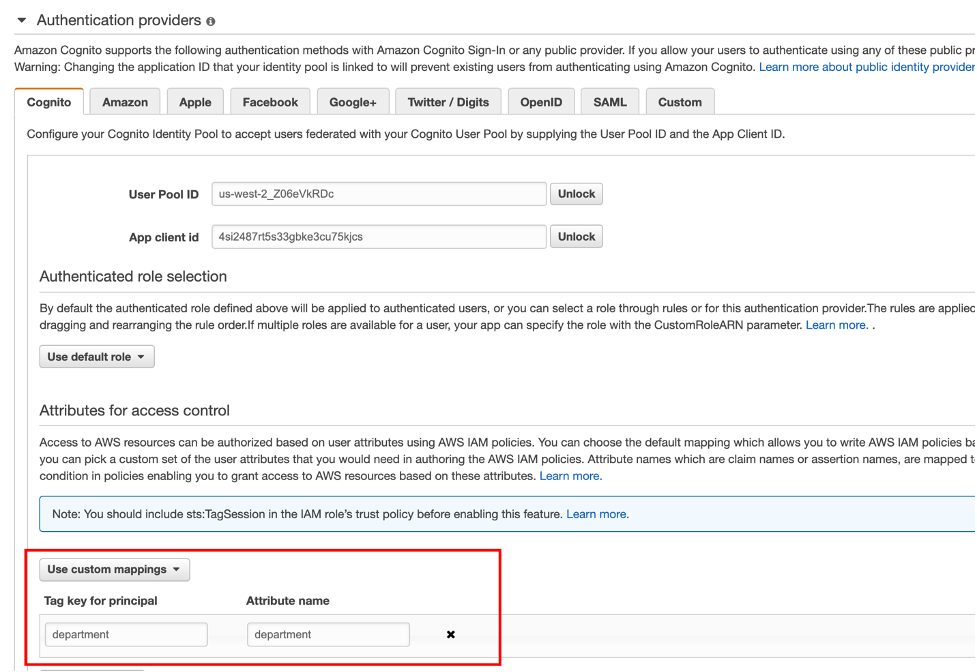
- Navigate to the Cognito console and select Manage Identity providers. Click on Edit Identity Pool. Expand the Authentication providers section and click on the dropdown button for Attribute access control Select the custom mappings item. Type department into both fields and then click on the save changes button.
- Edit the trust policy of IAM role mapped to your identity pool to allow “sts:TagSession”. Replace identity-pool-id below with your Identity Pool ID
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "cognito-identity.amazonaws.com"
},
"Action": ["sts:AssumeRoleWithWebIdentity", "sts:TagSession"],
"Condition": {
"StringEquals": {
"cognito-identity.amazonaws.com:aud": "identity-pool-id"
},
"ForAnyValue:StringLike": {
"cognito-identity.amazonaws.com:amr": "authenticated"
}
}
}
]
}
- Edit the IAM role mapped to your identity pool to allow listing objects under user’s department only as below
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": ["s3:List*"],
"Resource": "*",
"Condition": {
"StringEquals": {
"s3:prefix": "${aws:PrincipalTag/department}"
}
}
}
]
}
-
Now test accessing S3 once again by sign-out, sign-in again and then navigate to “Access S3” tab. Try to list files under the bucket directly (with empty prefix) or under any sub-directory other than the one defined in user’s department claim. You should see 403 error returning from this call indicating that access is denied.
-
Try listing files under “Engineering” sub-directory by providing “Engineering” in prefix. This call should succeed since you are trying to list files under the department that exists in token.
What happened here? Why can I list files under “Engineering” prefix but not under “Legal”?
Because user’s token has a “department” claim with the value “Engineering” (we added this claim from Pre Token Generation trigger).
And we configured the identity pool to pass this claim as session tag with the name “department”, then we modified the IAM policy to allow access only if the requested prefix matches the “department” session tag.
You have successfully completed Lab 3!